Learning cryptography and network security – Yo, check it! In this sick guide, we’re diving deep into the world of cryptography and network security. We’re talking about the secret codes, unbreakable locks, and ninja moves that keep your data safe from the bad guys. Buckle up and get ready for a wild ride!
From encrypting your messages to protecting your online accounts, cryptography and network security are essential skills in today’s digital jungle. We’ll break down the basics, show you how to use the latest tools, and give you the know-how to keep your data safe and sound.
Cryptography Fundamentals
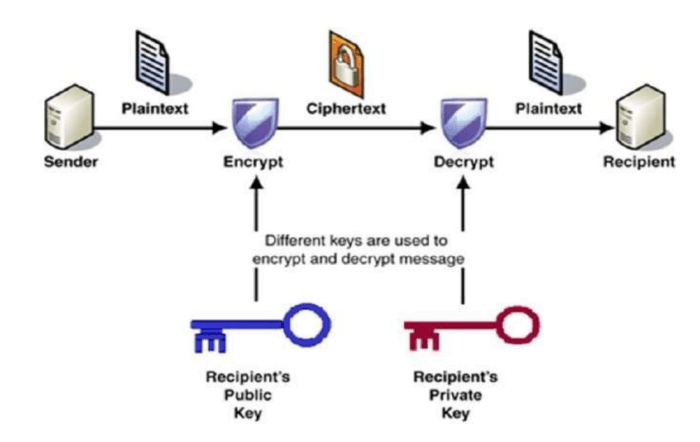
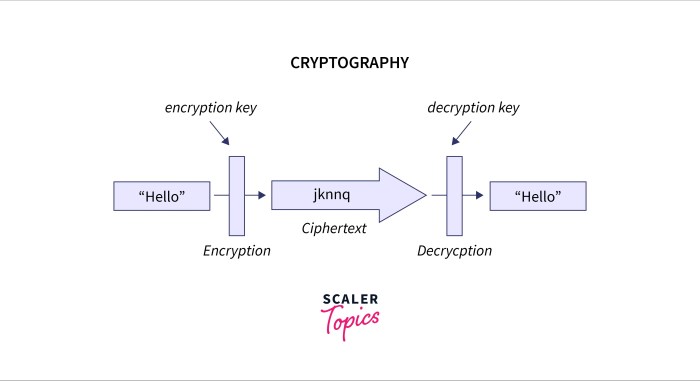
Yo, cryptography is the lit game of keeping your secrets safe. It’s like a secret code that only you and the cool kids you trust can crack.
The main players in this game are encryption and decryption. Encryption is when you turn your secret message into a scrambled mess, like taking a sick beat and turning it into a jumbled-up melody. Decryption is the opposite, where you take that mess and turn it back into the original dope track.
Yo, check this out. You already know about crypto and network security, right? But what about learning the stock market? It’s like the ultimate power move. Head over to How to Learn Stock Business for Beginners: A Comprehensive Guide to Financial Success . It’s the bomb.
Trust me, you’ll be hacking the stock market like a pro in no time while keeping your crypto and network security on lock.
Key Management
But hold up, how do you make sure only the right peeps can decode your message? That’s where key management comes in. It’s like having a special key that unlocks the secret door to your encrypted messages. Only those with the key can get in.
Yo, if you’re crushing cryptography and network security, you should check out learning about cryptocurrency mining . It’s like, the next level of digital security. Once you’ve mastered that, you’ll be the ultimate cyber ninja, keeping the bad guys out and the good vibes flowing.
Common Cryptographic Algorithms
There are a bunch of different ways to encrypt and decrypt messages, but some of the most popular are:
- AES (Advanced Encryption Standard): This is the go-to choice for encrypting everything from secret messages to your credit card info.
- RSA (Rivest-Shamir-Adleman): This algorithm is used for secure communication, like when you’re sending a message to your bestie.
- SHA-256 (Secure Hash Algorithm 256): This is a one-way street for data, turning it into a unique fingerprint that can’t be reversed.
Attacks on Cryptographic Systems
But hold your horses, cryptography isn’t invincible. There are some baddies out there trying to crack your codes. Here are some of the most common attacks:
- Brute Force: This is like trying every single key until you hit the jackpot.
- Cryptanalysis: This is the art of finding weaknesses in encryption algorithms to break them.
- Social Engineering: This is when someone tricks you into giving up your secret key.
Network Security Concepts
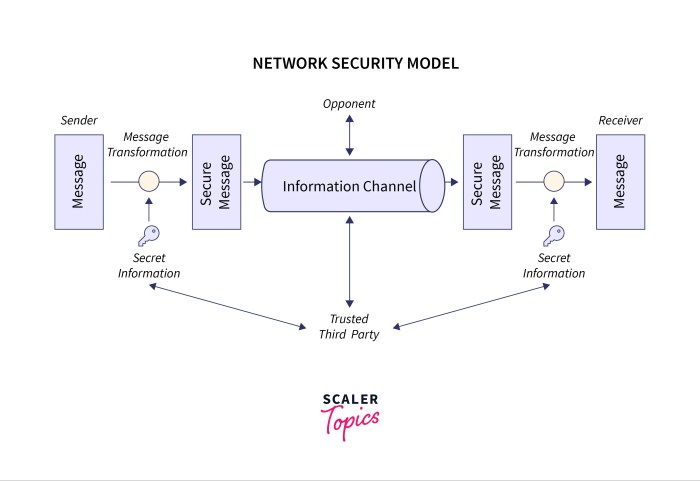
Network security is lit, y’all. It’s like the bodyguard for your network, keepin’ it safe from creeps and hackers. It’s super important ’cause it protects your data, like your passwords, bank info, and those embarrassing selfies. Without it, your network’s a sitting duck, wide open for attacks.
Common Network Security Threats
There’s a whole crew of threats out there lookin’ to mess with your network:
- Malware:Nasty software that sneaks onto your network and wreaks havoc.
- Hackers:Tech-savvy bad guys who try to break into your network for fun or profit.
- Phishing:Scams that trick you into giving up your personal info.
Network Security Vulnerabilities
These are the weak spots in your network that make it vulnerable to attacks:
- Unpatched software:When you don’t update your software, it’s like leaving the door unlocked.
- Weak passwords:Passwords like “12345” are like a welcome mat for hackers.
- Open ports:If you have ports open that you don’t need, it’s like leaving a window open in a thunderstorm.
Network Security Controls
Here’s the arsenal you need to protect your network:
- Firewalls:Like bouncers at a club, they check who’s coming in and out of your network.
- Intrusion Detection Systems (IDS):These watchdogs monitor your network for suspicious activity.
- Access Control Lists (ACLs):They decide who can access what on your network, like a VIP list at a party.
Cryptographic Tools
Cryptographic tools are the instruments we use to make cryptography happen. They’re like the hammers and nails of the crypto world, and they come in all shapes and sizes. Some are simple, like the trusty old Caesar cipher, while others are complex, like the mighty AES algorithm.
But no matter how simple or complex, they all share one common goal: to keep your data safe.
Yo, learning cryptography and network security is like, super clutch. It’s all about protecting your data from the bad guys. And if you’re really down, you should check out this dope article on learning about crypto . It’s got all the deets on how to keep your digital dough safe.
But back to the main event, learning cryptography and network security is like the ultimate defense against the dark side of the web.
Popular Cryptographic Tools and Libraries
There are a ton of different cryptographic tools and libraries out there, each with its own strengths and weaknesses. Here are a few of the most popular:
OpenSSL
A free and open-source library that provides a wide range of cryptographic functions.
GnuPG
A free and open-source tool for encrypting and decrypting data.
Yo, if you’re down for learning about crypto and network security, check out this beginner’s guide to cryptocurrency . It’s like, totally breaking down the basics of crypto in a way that even a newbie can get it. Then, you can come back to crushing cryptography and network security like a boss.
Bouncy Castle
Yo, learning crypto and network security is lit, but if you’re looking to get into the crypto game, check out learning about cryptocurrency trading . It’s like the ultimate cheat code to making mad money. But don’t forget, cryptography and network security are still the bomb for keeping your digital crib safe.
A Java library that provides a comprehensive set of cryptographic algorithms.
Examples of How to Use Cryptographic Tools
Using cryptographic tools is actually pretty straightforward. Here’s a simple example of how to encrypt a message using OpenSSL:“`openssl enc
- aes-256-cbc
- in message.txt
- out encrypted.txt
“`This command will encrypt the file “message.txt” using the AES-256 algorithm and save the encrypted data to the file “encrypted.txt”.
Yo, check it. Cryptography and network security are mad important nowadays, right? It’s like the key to keeping your data safe from those shady hackers. But hey, did you know that you can also make some serious dough by opening a credit server business? Peep this guide . It’s got everything you need to know about setting up your own biz and making bank.
After all, knowledge is power, and it’s all about protecting that knowledge in this digital age, fam.
Advantages and Disadvantages of Different Cryptographic Tools
Different cryptographic tools have different advantages and disadvantages. Here’s a quick rundown:
-*OpenSSL
Advantages
Free and open-source, widely used, supports a wide range of algorithms.
Disadvantages
Yo, check it, learning cryptography and network security is like, the bomb. It’s all about keeping your data safe and secure, right? But you know what’s even cooler? Learning cryptocurrency . It’s like, the future of money, man. You can invest in it, trade it, and even use it to buy stuff.
But don’t forget about cryptography and network security, ’cause they’re the foundation for all that digital cash flow.
Can be complex to use, not always easy to integrate with other applications.
Yo, learning crypto and network security is like, the bomb for keeping your data safe. But if you’re thinking of starting a cellphone service business, check out this . It’s got the lowdown on making bank in the cellphone biz.
Then, come back and keep grinding on your crypto and network skills – you’ll need ’em to protect your business.
-*GnuPG
Advantages
Free and open-source, easy to use, supports a wide range of algorithms.
Disadvantages
Not as widely used as OpenSSL, may not be as secure.
-*Bouncy Castle
Advantages
Free and open-source, written in Java, easy to integrate with Java applications.
Disadvantages
Not as widely used as OpenSSL or GnuPG, may not be as secure.
Yo, check it, learning about cryptography and network security is like the bomb for anyone who wants to be a cyber ninja. It’s all about keeping your data safe from the bad guys. And while you’re at it, why not dip your toes into learning about cryptocurrencies ? They’re like the digital gold of the future.
But don’t forget, cryptography and network security are the foundation for keeping your online life locked down tight. Stay safe, stay secure, and keep hacking like a boss!
Security Best Practices: Learning Cryptography And Network Security

Best Practices for Implementing and Managing Cryptographic Systems
To ensure the effectiveness and longevity of cryptographic systems, it’s crucial to adhere to best practices. These practices include:
- Use Strong Cryptographic Algorithms:Employ robust algorithms that align with industry standards, such as AES-256 or RSA-2048, to safeguard data.
- Manage Keys Securely:Protect cryptographic keys meticulously. Implement robust key management strategies, including regular rotation and secure storage.
- Implement Secure Protocols:Utilize secure protocols like TLS or SSH to establish encrypted communication channels.
- Regularly Monitor and Audit:Continuously monitor cryptographic systems to detect anomalies and vulnerabilities. Conduct regular audits to ensure adherence to best practices.
Common Security Pitfalls and How to Avoid Them
To avoid compromising the security of cryptographic systems, it’s essential to be aware of common pitfalls and take proactive measures to mitigate them:
- Weak Cryptographic Algorithms:Avoid using outdated or weak algorithms, as they may be vulnerable to cryptanalysis.
- Poor Key Management:Improper key management practices, such as weak keys or insecure storage, can compromise the entire system.
- Insecure Protocols:Utilizing insecure protocols or configurations can expose data to eavesdropping or tampering.
- Lack of Monitoring and Auditing:Neglecting to monitor and audit cryptographic systems can leave them vulnerable to undetected threats.
Staying Up-to-Date with Security Threats and Vulnerabilities
To stay ahead of evolving threats, it’s imperative to remain informed about the latest security threats and vulnerabilities:
- Subscribe to Security Alerts:Sign up for security alerts and advisories from reputable sources to receive timely updates on emerging threats.
- Attend Industry Events and Conferences:Participate in industry events and conferences to stay abreast of the latest advancements and best practices in cryptography and network security.
- Read Security Blogs and Publications:Stay informed by regularly reading security blogs, articles, and whitepapers from trusted sources.
- Collaborate with Security Experts:Consult with security experts or participate in online forums to gain insights and knowledge from industry professionals.
Emerging Trends
The realm of cryptography and network security is in a constant state of evolution, driven by emerging trends that are shaping the future of digital protection. These advancements have profound implications for organizations and individuals alike, demanding a keen understanding of their potential impact.
Quantum Computing
Quantum computing, with its mind-boggling processing power, poses a significant threat to traditional encryption methods. Quantum algorithms, like Shor’s algorithm, can swiftly crack codes that safeguard sensitive data, rendering current encryption standards obsolete.
Artificial Intelligence, Learning cryptography and network security
Artificial intelligence (AI) is a game-changer in network security, enhancing detection and response capabilities. AI-powered systems analyze vast amounts of data, recognizing patterns and anomalies that might elude human analysts. They automate threat detection, reducing response times and bolstering overall security.
Cloud Security
Cloud computing’s explosive growth has introduced novel security challenges. With data and applications residing in shared environments, protecting them becomes paramount. Cloud security solutions focus on access control, data encryption, and robust authentication mechanisms to safeguard sensitive information in the cloud.
Blockchain
Blockchain technology, renowned for its immutability and transparency, has found its way into cryptography and network security. Its decentralized nature and cryptographic underpinnings enhance data integrity, ensuring the authenticity and reliability of digital transactions and records.
Internet of Things (IoT) Security
The proliferation of IoT devices has expanded the attack surface for cybercriminals. These interconnected devices often lack robust security measures, making them vulnerable to exploitation. IoT security involves securing these devices and their communication channels to prevent unauthorized access and data breaches.
Final Summary
So, there you have it, folks! Cryptography and network security are like the secret sauce that keeps your digital life safe and secure. Whether you’re a tech wizard or just trying to protect your precious selfies, this guide has got you covered.
Stay tuned for more updates and tips on how to stay ahead of the hackers and keep your data out of the wrong hands!
Expert Answers
What’s the deal with cryptography?
Cryptography is like a magic spell that turns your data into unreadable gibberish. It’s the secret code that keeps your messages safe from prying eyes.
Why do I need to know about network security?
Network security is like a fortress that protects your computer and data from bad guys trying to sneak in and steal your stuff.
What are some cool tools for cryptography?
There are tons of awesome tools out there, like OpenSSL and GPG, that make it easy to encrypt and decrypt your data.





